Protecting Patient Data: Cybersecurity Tips for RCM Teams
Learn why hackers have been increasingly targeting the healthcare space recently, and explore the best cybersecurity tips RCM teams can implement to safeguard patient data against fraud.
September 18, 2025


Remember when financial institutions were public enemy number one for hackers? Or when credit card theft dominated headlines and data breaches felt like a Wall Street problem?
That era is long gone!
In 2024, healthcare became the most targeted industry for data breaches, surpassing finance for the first time. According to Kroll’s 2025 Data Breach Outlook, nearly a quarter of all cyber incidents last year affected healthcare organizations—from hospitals and clinics to billing vendors and specialty practices.
The reason? Bigger payouts in healthcare and relatively higher pressure to give in to cybersecurity threats.
In this blog, we’ll break down why healthcare has become the top target, and the technology and strategies that can help organizations protect their patient data.
Why Do Hackers Target Healthcare?
Unlike other industries, healthcare combines three traits that are catnip for hackers: valuable data, outdated systems, and extreme urgency.
At the heart of the issue is the incredible value of healthcare data. While a stolen credit card might let hackers access money, a bundle of Protected Health Information (PHI) opens the door to a lot more sensitive information.
But why is healthcare such an attractive target for attackers?
- PHI is premium currency: PHI is not just names and birthdays. It allows hackers access to the history of a person’s health, financials, and identity, all in one place, which may be used for identity theft, insurance fraud, or blackmail.
- The urgency is exploitable: Hospitals and practices can’t afford system downtime, making them more likely to pay ransoms quickly to restore operations.
- Legacy infrastructure creates weak points: Many providers still rely on outdated, disconnected systems that weren’t designed for today’s cybersecurity threats.
The Impact of Cyberattacks on Healthcare Organizations
The impact isn’t limited to stolen data, but also expands to operational paralysis.
Take the example of the Change Healthcare ransomware attack that left providers unable to process payments. In the days and weeks that followed, claims came to a standstill, eligibility checks stalled, and payment remits stopped flowing.

But the financial strain was only part of the fallout.
The investigation by the Office for Civil Rights (OCR) signaled that regulators now view these outages not just as IT issues, but as serious HIPAA and patient safety concerns.
And as AAPC put it in an analysis:
“The cyberattack on Change Healthcare caused far-reaching disruption, showing just how essential redundancy and resilience are in healthcare revenue cycle management.”
What Type of Patient Data is Valuable for Hackers?
For cybercriminals, the most valuable healthcare records and clinical documentation aren’t just lists of diagnoses or billing codes. They’re usually after complete, credential-rich profiles that can be used across multiple forms of fraud.
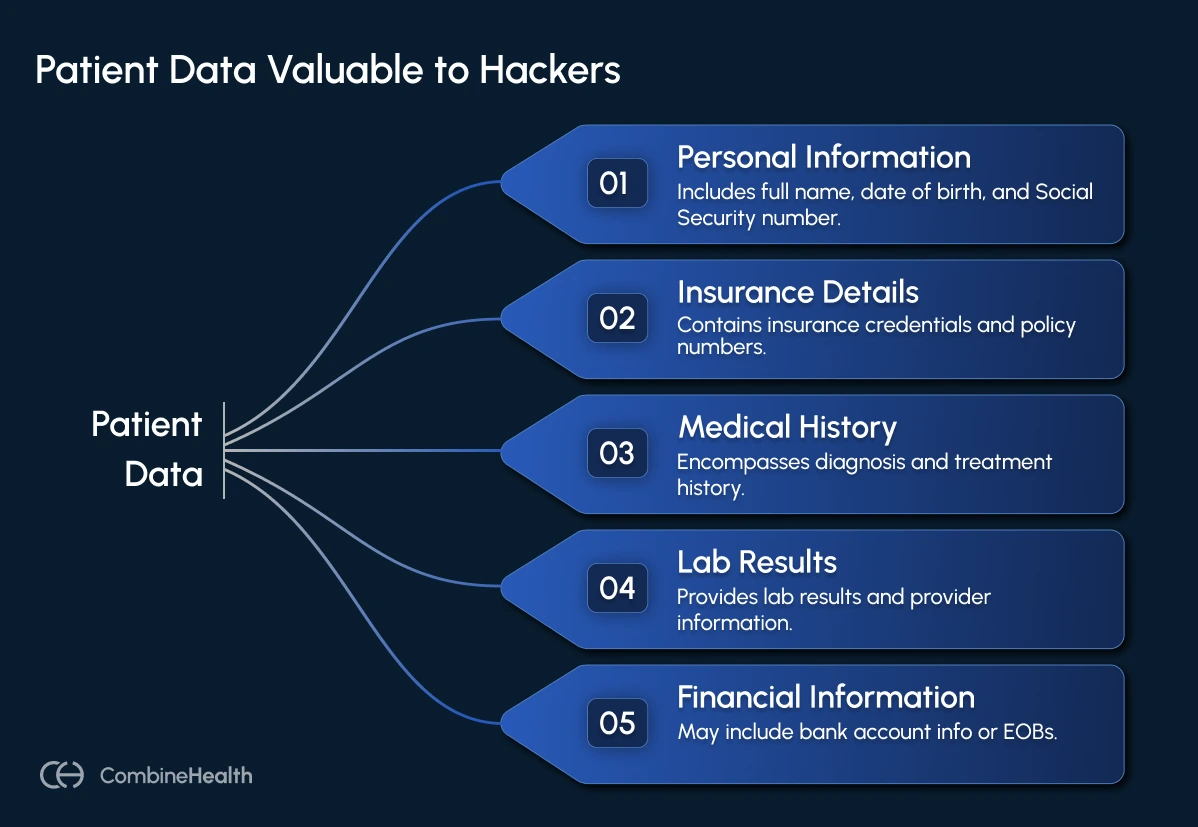
These full PHI records often include:
- Full name, date of birth, and Social Security number
- Insurance credentials and policy numbers
- Diagnosis and treatment history
- Lab results and provider information
- Contact details and, in some cases, bank account info or EOBs
But why are they sought after? Because they enable long-term identity theft, insurance fraud, fake medical claims, and even extortion. Here’s how:
- Complete medical records can sell for hundreds, even up to $1,000 if they’re fresh and comprehensive.
- Health insurance credentials bundled with identifying info have fetched prices between $500 and $1,200 on underground forums.
- Financial data tied to PHI, like EOBs, bank logins, or payment info, amplifies the risk, enabling both fraud and coercion.
- Sensitive condition data (mental health, oncology, reproductive care) is increasingly being used in blackmail and doxxing campaigns.
How Healthcare Organizations Can Strengthen Their Cybersecurity
Most healthcare organizations aren’t unprepared. They’re overwhelmed. Between fragmented systems, growing healthcare regulatory and governance pressure, and a constantly shifting threat landscape, even well-intentioned teams struggle to keep up.
But complexity doesn’t have to mean vulnerability.
Whether you're a hospital IT lead or a revenue cycle partner, there are focused, high-impact actions you can take right now to reduce exposure and improve continuity.
Here are three strategies worth exploring:
1. Outsource Compliance Management to a Cybersecurity and Compliance Services Company
For many healthcare organizations, keeping up with HIPAA’s Security Rule and evolving cybersecurity expectations is a full-time job. But most internal teams aren’t resourced to handle the responsibilities alone.
That’s where third-party cybersecurity compliance services like Accorian help RCM teams protect patient data through maintaining HIPAA compliance, end-to-end cybersecurity, and AI governance, all while ensuring resilience against evolving threats.
So, when evaluating a compliance partner, make sure the vendor offers:
- Support for comprehensive certifications like HIPAA, HITRUST, SOC 2, and ISO to ensure regulatory alignment.
- AI security and governance expertise—including AI risk assessments, global frameworks (like ISO 42001, NIST AI RMF), and third-party AI validation.
- Tailored HIPAA compliance services such as risk assessments, policy development, and safeguards specific to healthcare workflows.
- Cyber risk management capabilities like vulnerability scans, penetration testing, and incident response planning.
- Third-party risk oversight to vet vendors, especially AI-powered tools used in coding, analytics, or RCM operations.
2. Hire a HIPAA-Compliant RCM Services Company
If you're outsourcing parts of your revenue cycle—whether it's coding, billing, eligibility checks, or A/R follow-up—you're handing over access to some of your most sensitive data. That makes your choice of RCM partner not just a business decision, but a security one.
A HIPAA-compliant RCM solutions company goes beyond delivering services, but also infrastructure, processes, and oversight needed to protect patient information, maintain compliance, and keep operations running.
So, what does this look like in practice?
- BAAs (Business Associate Agreements) that clearly define security responsibilities, including how to use and protect patient data
- Demonstrated alignment with HIPAA requirements, including access controls, encryption, and audit logging
- Certifications like SOC 2 or HITRUST, showing that security controls are independently verified
- Multi-clearinghouse routing, so claims can still go out if one clearinghouse is compromised
Industry guidance from AAPC, HBMA, and HFMA stresses the importance of thoroughly vetting third-party partners. That means reviewing their security documentation, understanding their breach protocols, and confirming that their tech stack supports secure, patient-centered revenue cycle workflows.
3. Invest in an AI RCM Software With Built-in Safeguards
The case of Change Healthcare breach shows just how fragile the healthcare tech stack can be when redundancy and compliance aren’t prioritized.
That’s why it’s no longer enough to focus on compliance at the policy level. Security and governance need to be embedded into every single billing transaction and at scale.
In high-volume RCM environments, tens of thousands of interactions flow through your systems each day: claim edits, prior auth decisions, remittance notices, denial codes. Hidden PHI exposures, coding missteps, or outdated payer logic can slip through the cracks, and the consequences can include not just delays, but HIPAA violations and revenue loss.
That’s where AI-driven RCM platforms, like CombineHealth, can handle complexity and compliance in real time.
Here’s what to look for:
- Privacy controls built in: Encryption, role-based access, and anomaly detection should be standard for all transactions involving PHI.
- Automated audit trails: Logging should run continuously in the background to support compliance reviews and incident tracking.
- Layered quality checks: AI outputs should be reviewed through a mix of confidence scoring, cross-model validation, and human oversight.
- Real-time documentation alerts: Systems should flag missing or risky information before a claim is submitted.

Shield Your Healthcare Organization from Security Breaches
Healthcare data breaches are more than IT headaches, as they disrupt operations, jeopardize patient safety, and put revenue at risk.
The good news is that by combining compliance-focused processes, secure RCM partnerships, and technology-driven safeguards, organizations can reduce exposure, protect patient data, and keep revenue cycles running smoothly.
Ready to see how advanced CombineHealth’s AI agents can safeguard your revenue cycle operations? Book a demo!
FAQs
1. Why is healthcare a top target for cyberattacks?
Healthcare combines highly sensitive patient data, outdated systems, and urgent operational needs. Hackers exploit these factors to steal PHI for identity theft, insurance fraud, and ransomware, knowing organizations often prioritize quick recovery over security.
2. When is investing in a HIPAA-compliant RCM software vendor a good choice?
AI-driven RCM platforms automate billing, claims, and compliance checks, embedding security into every transaction. Features like role-based access, automated audit trails, layered quality checks, and real-time alerts reduce errors, prevent PHI exposure, and scale efficiently for high-volume billing environments.
3. When should a healthcare organization outsource compliance management?
Organizations struggling to keep up with HIPAA Security Rule requirements or lacking dedicated compliance teams should consider outsourcing. Third-party compliance services conduct risk assessments, formulate policies, and implement protective measures, reducing regulatory exposure while allowing internal teams to focus on core operations.






.webp)